Highlight

Successful together – our valantic Team.
Meet the people who bring passion and accountability to driving success at valantic.
Get to know usSeptember 11, 2024

In today’s dynamic business landscape, organizations are continually confronted with evolving challenges and uncertainties. One such challenge is the ever greater regulatory focus on the comprehensiveness of organizations’ risk management programs, with many companies struggling with the accuracy, completeness, and timeliness of their data while facing constraints in human and financial resources dedicated to risk assessment. Our mission is to empower you to navigate this complex environment successfully, leveraging cutting-edge technology to develop a profound understanding of your risk exposure and implement effective, regulatory conform risk management programs using leading frameworks such as the Three Lines of Defense model.
In a recent project, our client aimed to transform their risk management program from an informal, reactive approach to a strategy-aligned, proactive one – akin to “building with fire-proof materials in the first place rather than putting out fires that have already started.” Previously, their approach lacked a cohesive process for capturing and evaluating risks, exhibited limited auditability, and relied on a patchwork of non-specific software tools. By addressing these issues, the client was able to create a more structured and effective risk management framework that not only better satisfied regulatory requirements but that was more aligned with the company’s strategy and better supported long-term growth and resilience.
The first step in developing an integrated risk management program is to ensure that the organization effectively captures and assesses the suite of risks it faces. This includes for example detailed information concerning the nature of the risk, the subsidiaries and/or geographical regions the risk is applicable to, the expected financial impact of the risk materialising, and the likelihood of its occurrence.
CCH® Tagetik’s analytical workspace provides significant design flexibility and functionality, which as described in an earlier article, is well-suited to the development of an intuitive, thorough, and robust solution for capturing and assessing an organization’s risks. In this article, we will build on our previous discussion and delve into greater detail regarding specific technical features of CCH® Tagetik that we have found particularly useful in the context of risk capture and assessment.
The Three Lines of Defence model is a widely adopted framework employed by many leading companies to organize risk management duties, bolster accountability, and establish distinct roles among those managing risks, overseeing functions, and providing independent verification. This model clearly separates the responsibilities of each of the three “lines”, ensuring independent oversight and accountability across all levels of the organisation. The first line of defence involves business operations, the second line encompasses inter alia the Risk and Compliance function, and the third line is Internal Audit, providing independent assurance.

CCH® Tagetik processes can be designed flexibly through different steps, each of which can have its own set of user rights, enhancing the effectiveness of each aspect of the Three Lines of Defence model. This flexibility plays a crucial role in allowing for a clear separation between the first and second lines of defence. For instance, both groups of risk stakeholders can input risks independently. The second line can review and validate the risks assessed by the operational team, with the process only being able to be submitted once formal approval by the second line has been obtained. This enables the second line to follow-up with the first line for clarifications and/or potential alterations to their (the first line’s) inputs.
Another way in which CCH® Tagetik functionality supports the Three Lines of Defence is through the use of different datasets and their constituent typologies within the Analytical Workspace (AWS). Within a given AWS dataset, different “typologies” can be created; these serve as staging tables for data as it moves through different steps in the process, thereby further helping to manage and segregate data inputted by the different risk stakeholders, which represents a direct application of the Three Lines of Defence model.
The clear separation of process steps and the assignment of different user rights provide the Internal Audit function, the third line of defence, with a clear trail of accountability that can be effectively audited. Moreover, CCH® Tagetik’s built-in audit functionality automatically tracks all system activities performed by both users and administrators.
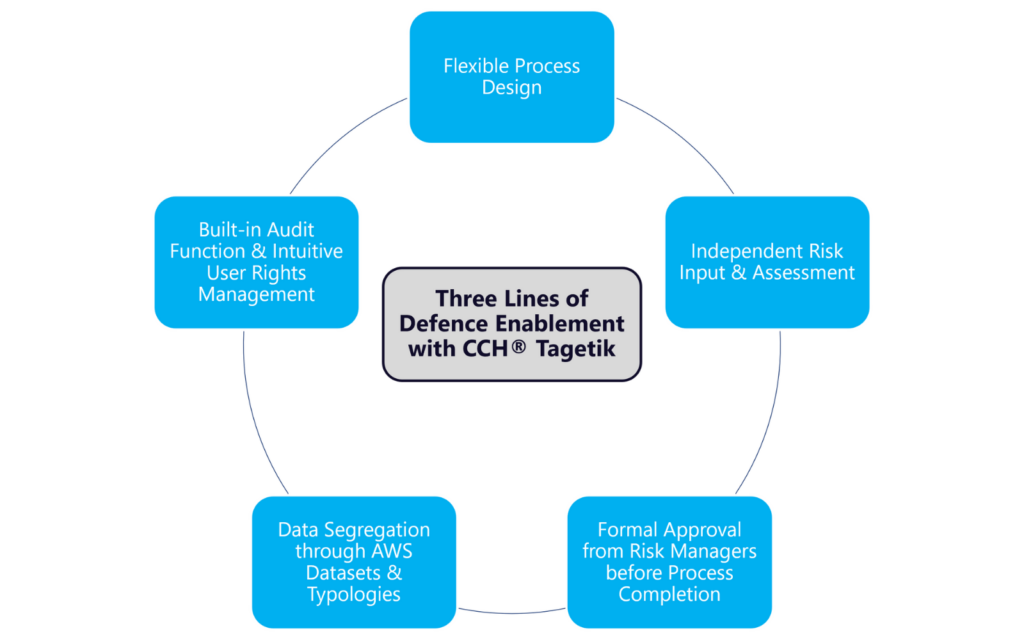
Some of the main advantages of employing the Three Lines of Defence model for risk management in tandem with CCH® Tagetik include:
Having a robust risk solution is essential, but to be truly effective it must also be easy and intuitive for business users to use. CCH® Tagetik excels in this area, offering a user-friendly interface along with various well-thought-out tools that create a solution that is not only technically sound but also user-friendly.
One prime example of this user-centric approach is the ability to readily incorporate different ways of fetching and transforming data into a process, such as data transformation packages (DTPs) or ETLs. Users simply need to click on the applicable icon and then “Run.” This will cause the DTP or ETL to obtain the desired data, transform it if necessary, and then load it to the relevant location. This streamlined process avoids laborious and error-prone manual procedures, such as the first line filling out a risk assessment template, sending it to the second line who then manually copies and pastes the information to their own version of the template.
Moreover, if desired, these DTPs/ETLs can also be directly incorporated into reports and run automatically whenever a user saves changes to the report, eliminating the need for separate tasks that need to be run individually. Additional functionalities that enhance the user experience include the ability to work with reports available in both the CCH® Tagetik web interface and in Excel, according to user preference, and the implementation of data validation rules that ensure user inputs align with requirements, with fields automatically highlighting any data quality issues.
Since integrating CCH® Tagetik into their risk management framework, our client has seen significant improvements in their ability to identify and assess risks promptly and accurately. The robust, flexible, and user-centric capabilities of CCH® Tagetik have provided the client with a more cohesive and proactive approach to risk management, that not only fulfills regulatory requirements but supports the company’s strategic objectives and long-term growth and resilience.
Moreover, the AWS is a strategic priority for CCH® Tagetik; the existing functionality it offers in the context of risk identification and assessment will only continue to be expanded upon. Are you also looking to enhance your risk management framework and explore the benefits of CCH® Tagetik? Connect with one of our experts and we’ll be happy to get the ball rolling!

Questions for our experts?
Do you have questions about the Three Lines of Defence model, want to improve your risk management, and discover the benefits of CCH® Tagetik? Get in touch with us.

Want to learn more?
Improve your risk management not only with the Three Lines of Defense model, but also with sustainable practices. Discover how CCH® Tagetik seamlessly integrates ESG reporting into your strategies.
Don't miss a thing.
Subscribe to our latest blog articles.